Activity
Mon
Wed
Fri
Sun
Feb
Mar
Apr
May
Jun
Jul
Aug
Sep
Oct
Nov
Dec
Jan
What is this?
Less
More
Memberships
OSINT Detective Skool
105 members • Free
3 contributions to OSINT Detective Skool
🎬 Movie Tip: Red Sparrow (2018) — When espionage weaponizes charm.
📰 Quick News Flash A U.S. Secret Service agent assigned to protect Vice President JD Vance has been placed on administrative leave after an undercover video showed him divulging sensitive security information including travel plans, protective procedures, and shift details, all while on what he believed was a romantic date. The woman he was seeing was actually an undercover journalist connected with James O’Keefe’s media group, and the interactions reportedly began after they matched on 🔥 Tinder. The Secret Service has suspended his clearance, revoked access to secure facilities, and ordered anti-espionage retraining for all personnel as the investigation continues. 🎥 Why Watch Red Sparrow Now If this recent scandal caught your attention, Red Sparrow is an eerie and thrilling reflection of how emotional leverage can become a tool of intelligence. In the film: - A Russian intelligence trainee is trained in psychological manipulation and seduction, not guns, to extract secrets. - Espionage isn’t about bullets; it’s about trust, attraction, and vulnerability. - Agents use relationships and support to gain access to classified information and influence decisions. The tactics in the movie echo real-world vulnerabilities: - Romantic or friendly interactions used to collect sensitive info - Trust exploited over time through emotional closeness - Platforms like dating apps now replacing old-school café meetings 🧠 Takeaway Espionage isn’t just about codes and covert ops. Sometimes, it’s about a swipe right. Red Sparrow isn’t just a spy thriller, it’s a reminder that social engineering and human relationships remain powerful intelligence tools in both cinema and real life. 🍿 Watch it with today’s headlines in mind.

🎬 Movie Tip: Focus (2015)
If you want to understand social engineering and OSINT in action watch Focus starring Will Smith and Margot Robbie. The film may look like a con artist romance, but Focus is a cinematic masterclass in human intelligence, psychological profiling, and information extraction through observation. You’ll see: - How body language reveals intent - How micro-details expose deception - How distraction and misdirection manipulate targets - How social context gives access to information others overlook Every great investigator knows: information isn’t always hidden, it’s performed. OSINT isn’t just about data. It’s about people.

⚠️ OPSEC LESSON: Attribution by Accident (Not Malice)
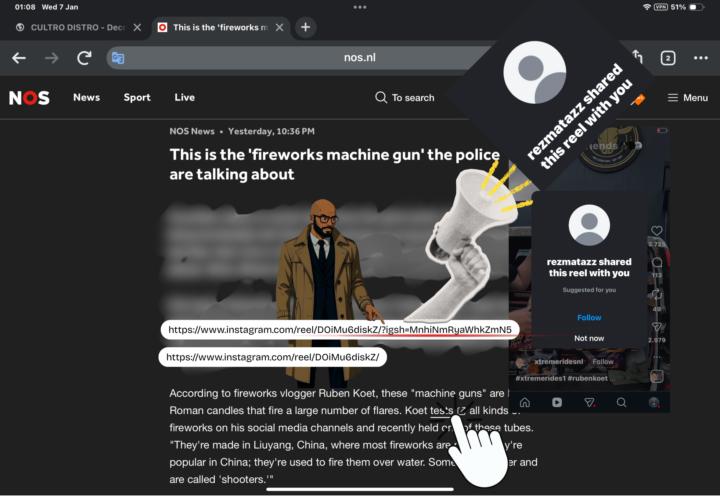
Today, NOS (Dutch state-associated media) published an article embedding an Instagram reel about dangerous fireworks. Let’s be clear from the start: - ❌ This was not malicious - ❌ This was not intentional - ❌ This was not dangerous in this specific case But it is instructive. What Happened? The embedded Instagram link opens with: “Shared by @username” This happens when: - A reel is shared directly from Instagram - The platform-generated URL retains a share attribution token - That URL is embedded without being cleaned As a result, a private user account becomes visibly linked to the dissemination of the content. Again: No intent. No wrongdoing. No immediate risk here. Why This Still Matters In this case, the topic was fireworks and public safety. Low sensitivity. Low risk. No real consequences. But the mechanism is the same mechanism that can become dangerous in other contexts. Think about investigations involving: - Corruption within the state - Corporate fraud - Organized crime or cartels - Militia or paramilitary groups - Intelligence services - Extremist or criminal networks - In those environments, attribution alone can be enough to: - Draw unwanted attention - Expose relationships - Identify intermediaries or sources - Create pressure, intimidation, or retaliation Not because someone did something wrong — but because they became visible. The OSINT & OPSEC Insight Social media platforms are not neutral pipes. They are attribution systems. When you share content directly from a platform: - The link may carry account-level fingerprints - Those fingerprints can travel far beyond your control - Third parties may publish them unintentionally This is not paranoia. This is how link analysis works. Practical Takeaway For everyday topics: - Usually harmless For sensitive research or investigations: - Potentially risky Best practice in sensitive contexts: - Strip tracking parameters - Use clean URLs - Screenshot with metadata removed - Describe content instead of linking - Assume anything public may be archived forever
1-3 of 3


