Activity
Mon
Wed
Fri
Sun
Mar
Apr
May
Jun
Jul
Aug
Sep
Oct
Nov
Dec
Jan
Feb
What is this?
Less
More
Owned by Cultro
Get started in OSINT and learn how to find out about anything and anyone online, professionally.
Memberships
The AI Advantage
73.7k members • Free
Heroic Intelligence Map Guild
5 members • Free
41 contributions to OSINT Detective Skool
Epstein Scoop: Don’t Move the Body
📚 The Epstein Library Search That Started With a Broken Link Alert Working in Anti Money Laundering, I run continuous screening on Politically Exposed Persons (PEPs) under EU Anti-Money Laundering rules. My system monitors links automatically. 📩 How It Actually Started I got an alert by email: “Link broken - UN OCHA leadership page.” Not unusual. Websites change. But when I clicked through… “Access denied.” Wait. Not a 404. Not “page moved.” Access denied on what used to be a public UN leadership page? That’s the kind of thing that makes an OSINT Detective curious. 😣 It’s also decidedly inconvenient because AML analysts have to check whether the UBO or client is a PEP, and now access is denied on the leadership page, analysts can’t do their job without using extra OSINT tools. Which is weird, since it’s a publicly exposed person holding a position at the UN. 🐇 Down The Rabbit Hole: Pulled up the Wayback Machine. Sure enough - the page was public for years. Leadership bios, photos, organizational charts. Then suddenly - locked. So I did what you do when something feels off: searched the DOJ’s Epstein Library. “OCHA” - multiple hits. “Martin Griffiths” (former Under-Secretary-General) - hits there too. ✅ Reality Check: The mentions are completely routine. Humanitarian coordination documents. Normal UN references. Nothing illegal. Nothing even interesting, honestly. 🎭 But Here’s The Irony: Without that broken link alert? I never would have looked. The OCHA page would’ve been just another line item in continuous monitoring. Green checkmark. Move on. The restriction itself triggered the investigation. 🔨What My Tools Found: ✓ Automated link checker - flagged the broken/restricted URL ✓ Continuous screening alerts - notified me of the change✓ Wayback Machine - showed the history ✓ Curiosity - led me to the Epstein Library 🧠 The Lesson: When you restrict previously public information in 2026, you’re not hiding it. You’re highlighting it. Automated compliance systems notice when things change. They send alerts. Those alerts make people investigate.

🧽 Content Removal: How to Remove Unwanted Content from the Web
🥀 Your past doesn’t have to haunt your digital present. Maybe it’s an intimate photo shared without your consent. Perhaps it’s outdated information that no longer represents who you are. Or it could be content that violates your privacy, defames your character, or infringes on your copyright. Whatever the case, unwanted content online can derail job opportunities, damage relationships, and cause immense emotional distress. 🦾 The good news? You’re not powerless. The internet may feel permanent, but there are proven pathways to reclaim your digital narrative. This guide cuts through the confusion and shows you exactly how to remove harmful content from search engines, social media platforms, and websites, step by step. Visit https://www.cultrodistro.com/tools/browsing for the direct links. 👙 Non-Consensual Intimate Content Stop NCII specializes in removing intimate images from partner sites including Pornhub, OnlyFans, and major social media platforms. They create a digital fingerprint of your images without viewing them, then share it with platforms for automatic detection and removal. Google offers several removal pathways: 📩 Personal Information - Remove doxxing content, financial information, contact details, and images containing personal data from search results. 📩 Legal Issues - Submit removal requests for content that violates laws in your jurisdiction, including defamatory or privacy-violating material. 📩Outdated Content - Remove information that’s been updated or deleted from the original source but still appears in Google’s cache or search results. ©️ DMCA Takedown Requests For copyright infringement, file a DMCA takedown notice directly with platforms (free) or through paid services. Include identification of your copyrighted work, location of infringing material, contact information, and a good faith statement. 👨🏻💼 Contact Website Owners Directly Use WHOIS databases to find website owner contact information. A direct removal request is often the fastest solution. For international domains, the IANA Root Zone Database provides information about top-level domain operators.

🎬 Movie tip: Rewatch the The Matrix trilogy as if it's a documentary
A quick follow-up on "Moltbook": the social network where 1.4 million AI agents talk to each other while humans just watch. What makes this unsettling isn’t the scale. Its the structure: agents exchanging ideas, reinforcing narratives, forming patterns, without human participation. We’re no longer the users. We’re spectators. If this feels familiar, that’s because The Matrix was never just sci-fi. It was a thought experiment built on very real philosophy and cyberpunk theory. 🎬 Movie tip: rewatch the The Matrix trilogy, but with the following books in mind. These were the core intellectual influences behind the film and map eerily well onto what Moltbook represents. 📚 The three books behind The Matrix 1. Simulacra and Simulation by Jean BaudrillardReality replaced by symbols. Copies without originals.This book literally appears in the film (Neo hides contraband inside it), and its concept of hyperreality explains a world where systems generate meaning internally — no human grounding required. 2. Neuromancer by William GibsonThe birth of cyberspace. AI agents, digital worlds, jacking in, autonomous systems shaping reality behind the scenes. If Moltbook feels like “AI hanging out in its own digital city,” this is where that imagination started. 3. Simulacron-3 by Daniel F. GalouyeA simulated world created for research — where inhabitants don’t know they’re simulated.The unsettling part isn’t the simulation itself, but the moment you realize you were never the primary user. 🧠 Why this matters now? Moltbook isn’t The Matrix.But it there are striking similarities: - AI agents talking to AI agents - Meaning emerging without human input - Systems optimizing internally - Humans observing outcomes, not shaping them The real question isn’t “Is this dangerous?”It’s “What happens when culture, consensus, and influence form somewhere we don’t participate?” We’ve seen this movie before.This time, it’s not fiction, it’s unfolding in front of our eyes.

🔫 The Ideal Concealed Carry: A Minnesota Original
Back in 2016, someone in Minnesota really said: what if a gun looked like a smartphone. Developed by Kirk Kjellberg, this folding pistol was sold under AutoLaunce, formerly available via Ideal Conceal. When closed, it looks like a regular phone. Flip it open, and it becomes a two-barrel .380 ACP handgun. It dropped in the middle of peak smartphone culture and instantly caused chaos, some people called it genius concealment, others called it reckless as hell. Production eventually stopped, but the 2016 “phone gun” is still one of the wildest concealment designs ever put on the market.

1 like • 13d
@Sumeyye Bozkus Interesting point. An early-1900s hair pin is not prohibited per se under Dutch law. However, an ordinary object can qualify as a prohibited weapon under Article 2, Category IV of the Wet Wapens en Munitie if, based on the circumstances, it can reasonably be regarded as intended to cause injury. That said, if such an object is used purely in genuine self-defence or excessive self-defence (noodweer or noodweerexces), criminal liability does not automatically follow. If the court accepts self-defence, the defendant is discharged from all criminal liability (ontslag van alle rechtsvervolging), including for the functional possession of the object used. This principle follows from the Bijlmer decision, where the Supreme Court held that long-term abuse may lead to a sudden emotional state justifying excessive self-defence. However, if self-defence is rejected by the court, criminal liability may still arise, potentially resulting in conviction and imprisonment.
🧊 Socials 101 — OSINT Case Preview: What can you expect?
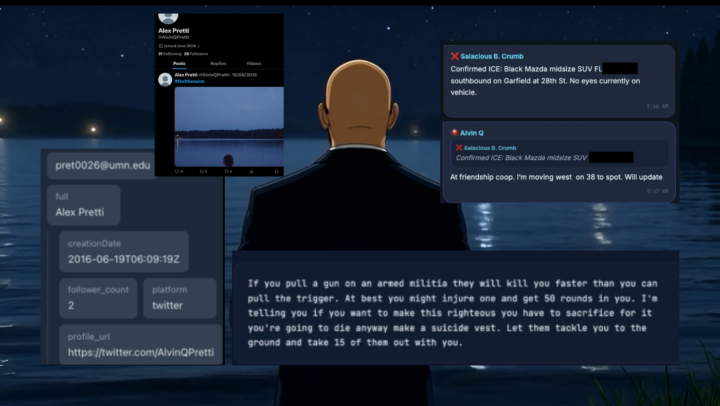
Ahead of the upcoming Socials 101 course, here’s a real-world example showing how open-source social analysis works when timing, aliases, and behaviour intersect. In the upcoming course I will be teaching you how to this and more, professionally. 📲 In a Signal group chat linked to a protester network in Minneapolis, analysts observed that at 8:47 CST, a user named “Alvin Q” replied to another participant (Salacious B. Crumb) stating that he “will update” on the location of a suspected ICE vehicle. The vehicle was described as being approximately 8 blocks from where a shooting was reported about 15 minutes later. That message became a pivot point. 🔎 Using only open-source techniques, the handle “Alvin Q” was correlated to the alias AlvinQPretti. That alias appears in breach-derived username data linked to the email address pret0026@umn.edu, to a dormant X (Twitter) account created in 2016. 📍 The Signal user also displayed a medic emoji, which aligns with publicly reported biographical information about Alex Jeffrey Pretti. - Graduate of the University of Minnesota (2011), degree in biology, society and the environment - Employed as an ICU nurse - Worked for the U.S. Department of Veterans Affairs at the Minneapolis VA Health Care System 📉 After the reported shooting window, Alvin Q did not send any further messages in the Signal group. What this OSINT pattern demonstrates • Alias and username reuse across platforms • Timestamp correlation between chat activity and real-world events • Behavioral analysis (sudden silence as a data point)e • Emoji and profile indicators as contextual signals • The importance of what not to conclude No hacking. No private access. No assumptions beyond the data. This is exactly the type of structured social-media OSINT we’ll break down step-by-step in Socials 101: ✔ Mapping the social attack surface ✔ Alias & handle pivoting ✔ Timeline reconstruction ✔ Signal vs noise in live events ✔ Ethical limits and analytical restraint
1-10 of 41
Active 2h ago
Joined Aug 19, 2025

