
Write something
AI Projects
Here are some AI projects if your interested. Everything Claude Code - https://github.com/affaan-m/everything-claude-code agent-browser - https://github.com/vercel-labs/agent-browser DeepTutor: AI-Powered Personalized Learning Assistant - https://github.com/HKUDS/DeepTutor Qwen3-TTS - https://github.com/QwenLM/Qwen3-TTS 1Code - https://github.com/21st-dev/1code Antigravity Awesome Skills - https://github.com/sickn33/antigravity-awesome-skills OpenClaw on Cloudflare Workers - https://github.com/cloudflare/moltworker Awesome OpenClaw Skills - https://github.com/VoltAgent/awesome-openclaw-skills zerobrew - https://github.com/lucasgelfond/zerobrew nanobot: Ultra-Lightweight Personal AI Assistant - https://github.com/HKUDS/nanobot Claude HUD - https://github.com/jarrodwatts/claude-hud skills - https://github.com/vercel-labs/skills HeartMuLa: A Family of Open Sourced Music Foundation Models - https://github.com/HeartMuLa/heartlib PDFCraft - https://github.com/PDFCraftTool/pdfcraft LingBot-World: Advancing Open-source World Models - https://github.com/Robbyant/lingbot-world Trellis - https://github.com/mindfold-ai/Trellis OpenViking: The Context Database for AI Agents - https://github.com/volcengine/OpenViking Maestro - https://github.com/its-maestro-baby/maestro
Agentic AI EcoSystem Overview
Good Evening All, I have recently created an overview of my entire Agentic AI Ecosystem so far and though some of you may wish to have a read. There is also a really good diagram to follow as you ready through it. Let me know your thoughts and ideas for any future use cases. https://wiki.prismsecure.online/en/AgenticAIEcoSystemOverview
2
0
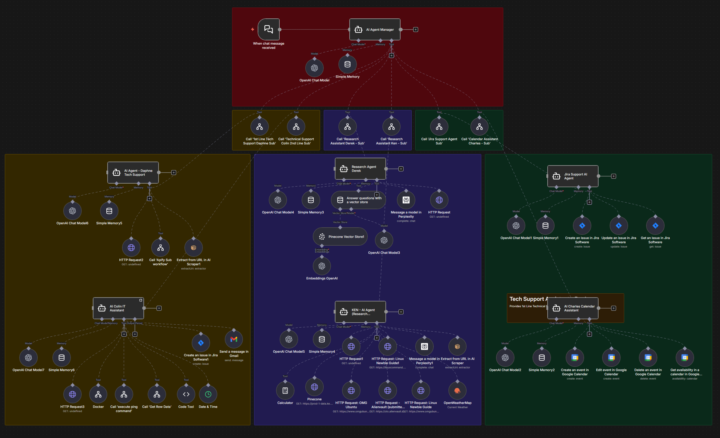
n8n Exposure
Hey everyone, I’m exploring the safest way to expose an n8n instance to the internet so it can work with external services, and I’d love your input on hardening practices. I see a lot of deployment guides but far fewer security deep-dives. My setup - Proxmox cluster - Virtualized pfSense - Ubuntu 24.04 server (Docker) - Official n8n Docker behind Traefik - Isolated VLAN for this stack (blocked from other VLANs) - Cloudflare Tunnel connector on a separate VM (same LAN) - UFW: default-deny inbound; SSH allowed only from a specific IP - Docker publishes 80/443 for Traefik (UFW doesn’t interfere with Docker’s chain) - SSH via keys (no passwords) - Fail2Ban enabled What I’m asking: 1. What additional layers would you add for an internet-facing n8n (especially auth, network controls, rate-limiting)? 2. Any Traefik or Cloudflare Tunnel rules you recommend (mTLS, WAF, IP allow-lists, Cloudflare Access, etc.)? 3. Gotchas you’ve hit with Docker/UFW/Traefik interplay or n8n webhooks under tunnels? 4. Monitoring/logging tools you’ve found helpful for detecting abuse (and sane defaults for alerts)? 5. Goal: A practical, defense-in-depth checklist others can reuse. Suggestions, examples, and “don’t do this” stories are all welcome. Thanks in advance!
n8n AI Integrated Workflows
I have been dabbling with this today.......... n8n Quick update, I spent yesterday (Sunday) creating a few basic workflows, validating them and then expending them out. I have n8n self hosted, using npn reverse proxy with lets encrypt ssl. One this to note, if you do self host make sure you enable web sockets in your nginx proxy manager entry otherwise it will lose server connection. Mondays update: create my first more complex workflow that checks a set of defined URL's , checked for status code 200, then depending on whether it is successful or not send a predefined message via telegram. @Brandon Lee this would make a great video series, hint hint :-)
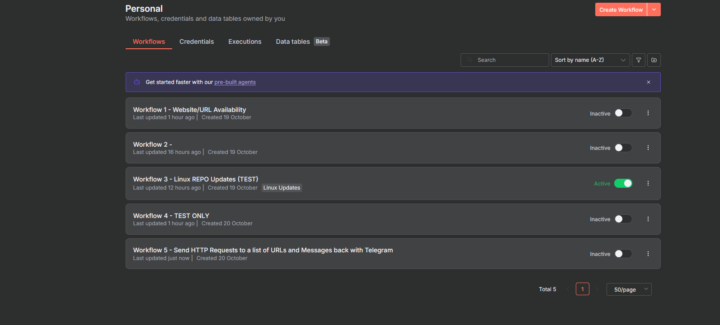
A new list of self-hosted AI tools for the home lab
Anyone using these tools in their home labs now? https://www.virtualizationhowto.com/2025/10/best-self-hosted-ai-tools-you-can-actually-run-in-your-home-lab/
1-11 of 11

skool.com/homelabexplorers
Build, break, and master home labs and the technologies behind them! Dive into self-hosting, Docker, Kubernetes, DevOps, virtualization, and beyond.
Powered by







