Activity
Mon
Wed
Fri
Sun
Mar
Apr
May
Jun
Jul
Aug
Sep
Oct
Nov
Dec
Jan
Feb
What is this?
Less
More
Memberships
Learn Online Security
34 members • Free
4 contributions to Learn Online Security
What topics would you like to know about?
As we consider future podcast topics we'd like to hear your ideas. Share them here and one lucky member might get their idea covered!

There is a shark in the water...^...
One problem with constantly focusing on security issues is that we become a negative voice. Every post is, "watch out for this", "these people are coming after you". I recently spoke with another podcast host who has the same problem. We decided that some, maybe not all, of the topics can be covered with a focus on hope or self-improvement vs. "the sky is falling". The other problem is that doom-and-gloom content gets more views. I would rather provide you with hope and a lifeboat than a finger pointing at a shark. What do you think?
De-cluttering is all the rage.
What happens when that impromptu 10-minute power clean turns into a data breach? When it comes to business security, most owners focus on software, firewalls, and encryption. But one often-overlooked risk lies in how people handle devices at the end of their life—from old laptops and phones to printers and fax machines. Every device that stores or transmits information is a potential leak point, and the human factor plays a critical role in keeping that data safe. What device were you surprised to learn was a potential security risk?
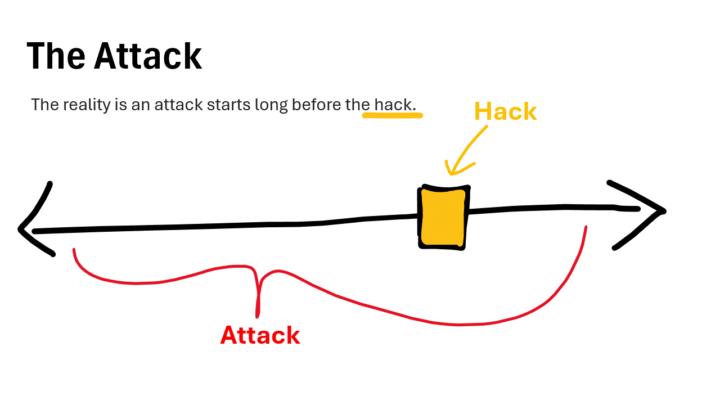
Don't miss the attack
Most of the time we focus on the hack or scam or theft and forget that there is a bigger picture here. We have to see the attack as a process and not a simple event. There are preplanned, well thought out, processes. The earlier we can pick up on the process, the quicker we can thwart the attack.
1-4 of 4
Active 40d ago
Joined Sep 11, 2025


